| Introduction to Data Communications | ||
|---|---|---|
|
|
41d. Bridge Methodologies (cont'd) | Next |
The Spanning Tree Protocol was developed to address the problems of loops in Transparent Bridging. The IEEE 802.1D (Institute of Electrical and Electronic Engineers) committee formed the Spanning Tree Protocol.
The Spanning Tree Protocol (STP) converts a loop into a tree topology by disabling a bridge link. This action ensures there is a unique path from any node to every other node in a MAN or WAN. Disabled bridges are kept in stand-by mode of operation until a network failure occurs. At that time, the Spanning Tree Protocol will attempt to construct a new tree using any of the previously disabled links.
The Spanning Tree Protocol is a Bridge to Bridge communication where all bridges cooperate to form the overall bridge topology. The Spanning Tree algorithm is dynamic and periodically checks every 1 to 4 seconds to see if the bridge topology has changed.
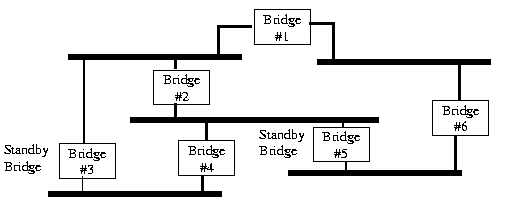
Bridge #3 & #5 are stand-by bridges and have their links disabled. This results in only 1 path to each network segment.
Each bridge is assigned an arbitrary number to assign priority to the bridge in the internetwork. The number is concatenated with the bridge MAC address. The MAC address is used as a tie breaker mechanism if 2 bridges have the same priority. The lower the assigned number the higher the bridge priority.
During initial power-up, a Bridge Protocol Data Unit (BPDU) is flooded out each network port of the bridge. The BPDU contains the current spanning tree root, the distance to the root (measured in hops through other bridges), the bridge address information and the age of the information in the BPDU. Bridge priorities are usually manually controlled so as to configure the traffic flow over the internetwork over a preferred path.
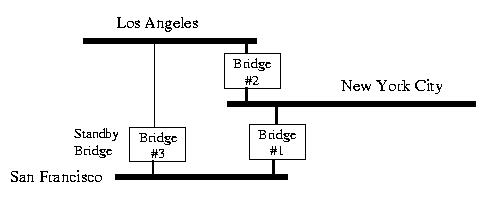
Problems can arise where the Spanning Tree Algorithm may select a path from Los Angeles to New York City and back to San Francisco rather than the preferred route of Los Angeles to San Francisco.
| Introduction to Data Communications | ||
|---|---|---|
|
|
Table of Contents | Next |